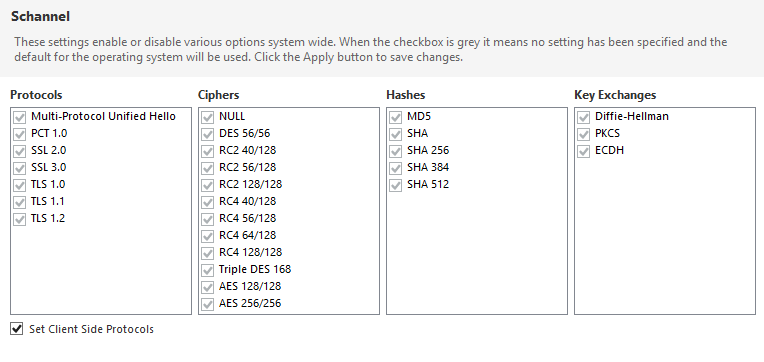
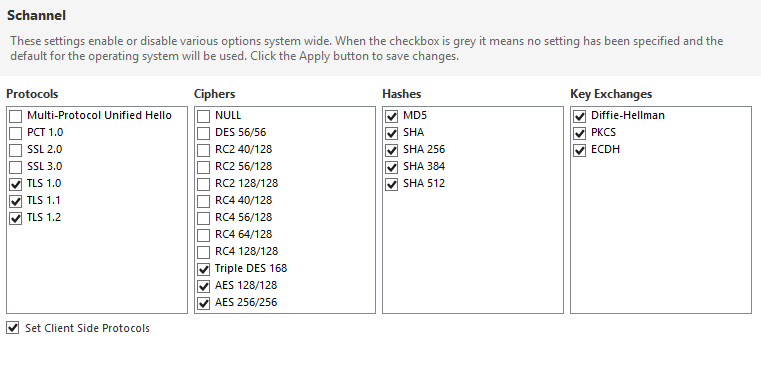
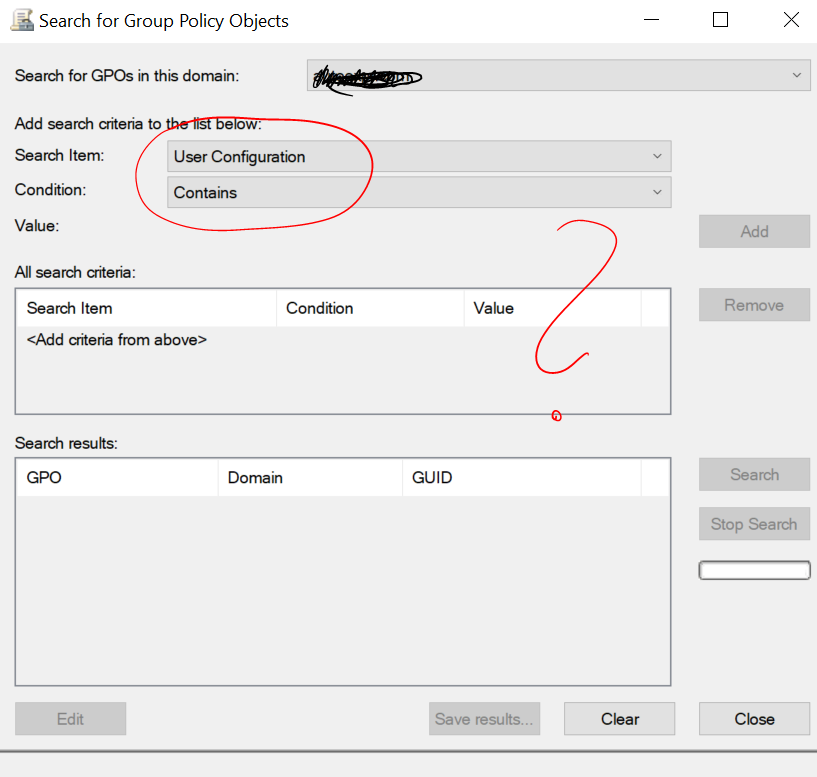
How fix the problem in the picture ? Affected server was Sxxxxxxx.
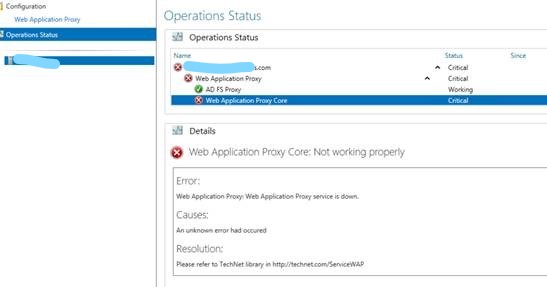
Open up Remote Access management console and You see red. The red color is nice but in this case it means that something is wrong.
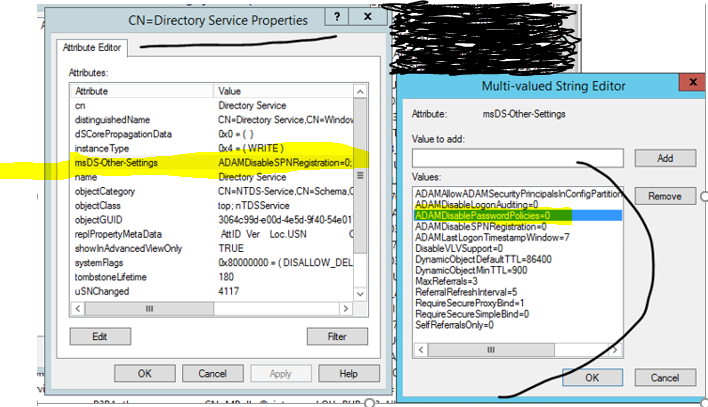
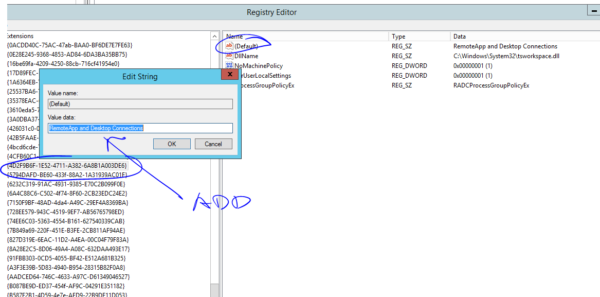
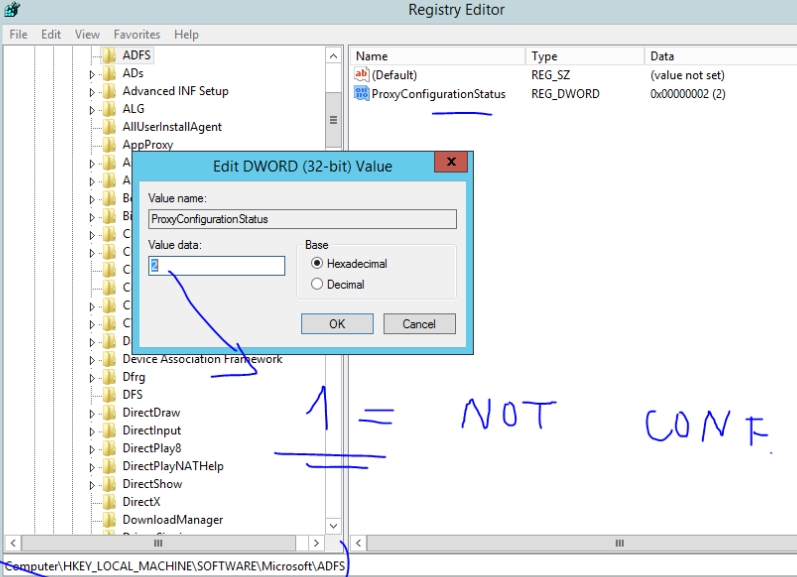
We need to reset WAP configuration, in Registry we have to change value 2 = configured to the Value 1 = not configured
Use powershell.exe – Install-WebApplicationProxy -CertificateThumbprint “xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx” -FederationServiceName “xxxxxx.com” (but it did not work for me same good as GUI for server ADFS 3.0 S2K12 R2 🙁 ….)
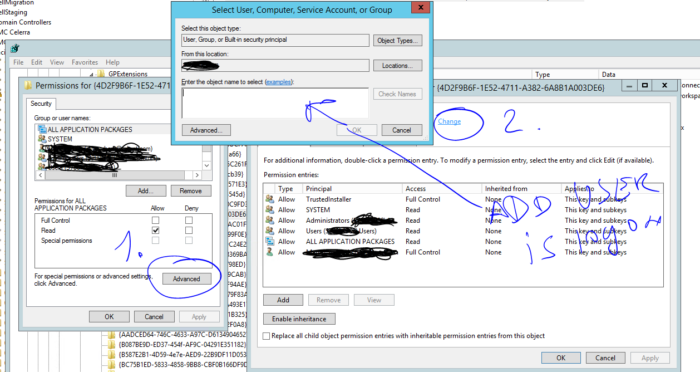
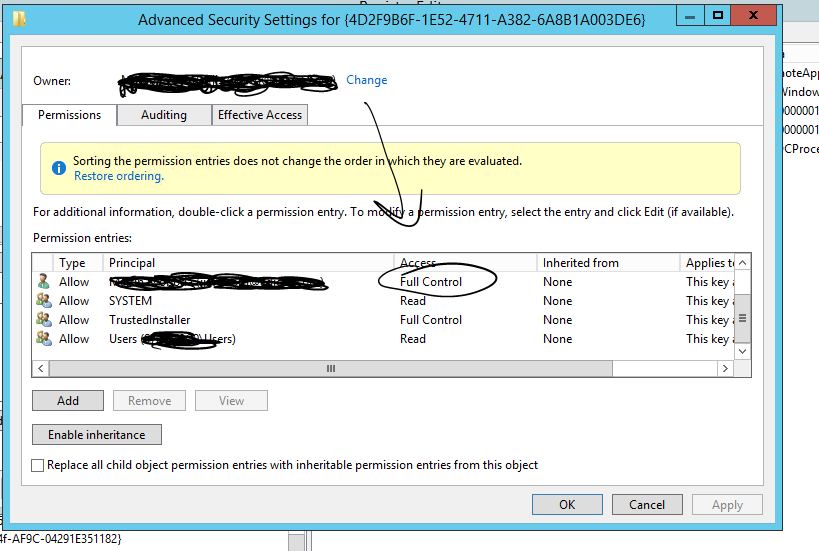
or through console Remote Access management we configured WAP again. It requires name of ADFS service – xxxxxxxxxxx.com, usually service account – axxxxxx and choose the right certificate – right ADFS certificate with name xxxxxxxxxxx.com. Although we did this, the service tried to use different, self-signed certificate , In ADFS event log we could see „Unable to retrieve proxy configuration data from the Federation Service + thumbprint of bad certificate not our ADFS certificate “ In mmc.exe we could see only the certificate for MS SCOM, xxxxxxxxxxx.com and some expirated self-signed certificates but we could not see the certificate with thumbprint found in event log. By Powershell we could list it (example is below), we found bad certificate + others and we removed all certificates self-signed certificate.
Get-WebApplicationProxySslCertificate, Get-ChildItem -Path cert:\LocalMachine\My | FL FriendlyName, Thumbprint, Subject, NotBefore, NotAfter
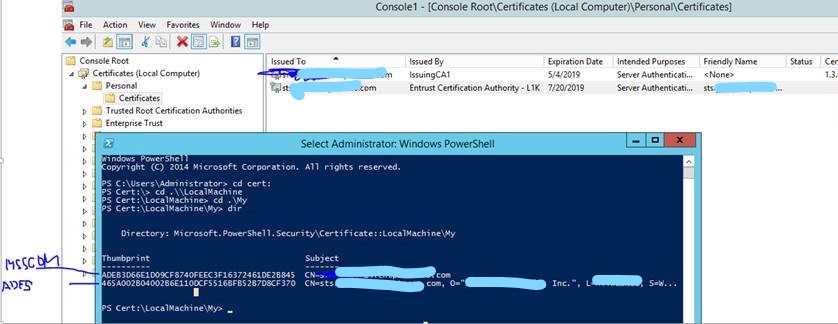
When we removed the self-signed certificates, we tried to complete the wizard again and it was success
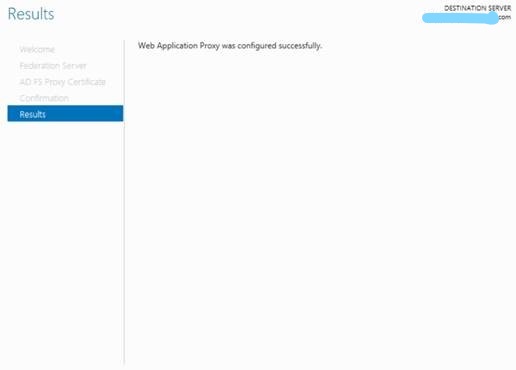
Now it is working well. Do not worry that we see server xxxxxx twice, we could see it because in my case we configured WAP after the server has been configured with postfix (full computer name), because for MS SCOM monitoring it is require.
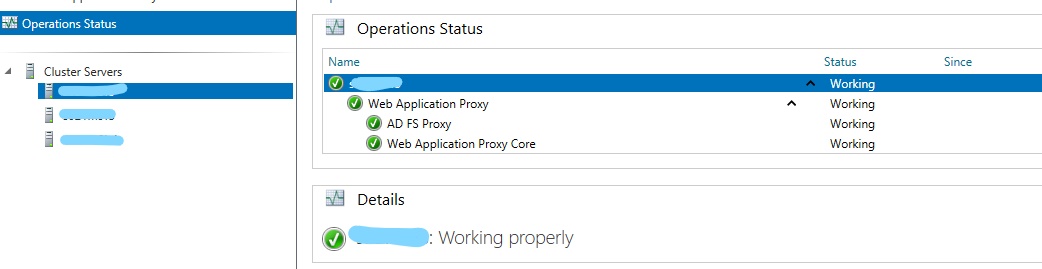
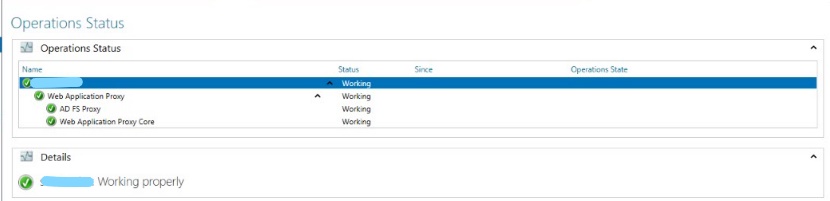
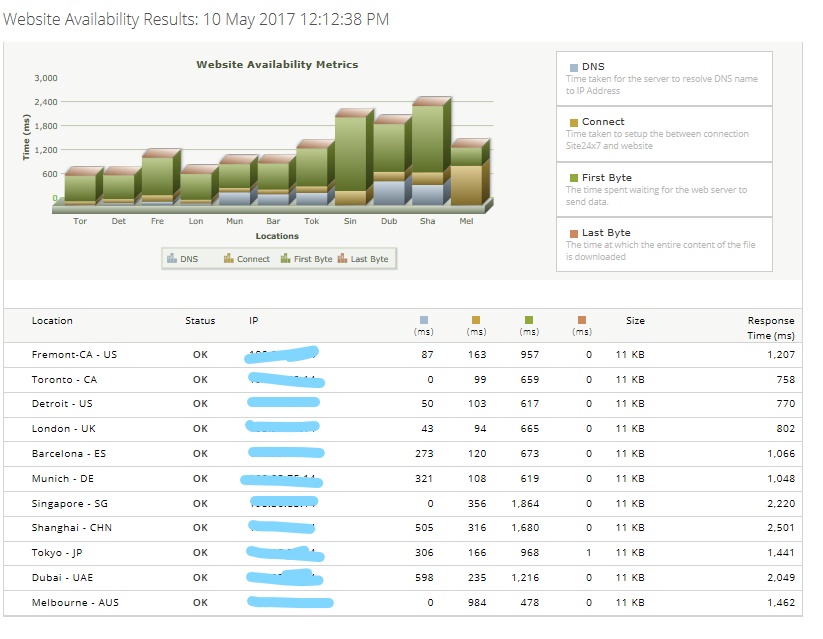
The result of testing availability https://[name of your ADFS]/adfs/ls/IdpInitiatedSignon.aspx from internet. Tested from page – https://www.site24x7.com/check-website-availability.html